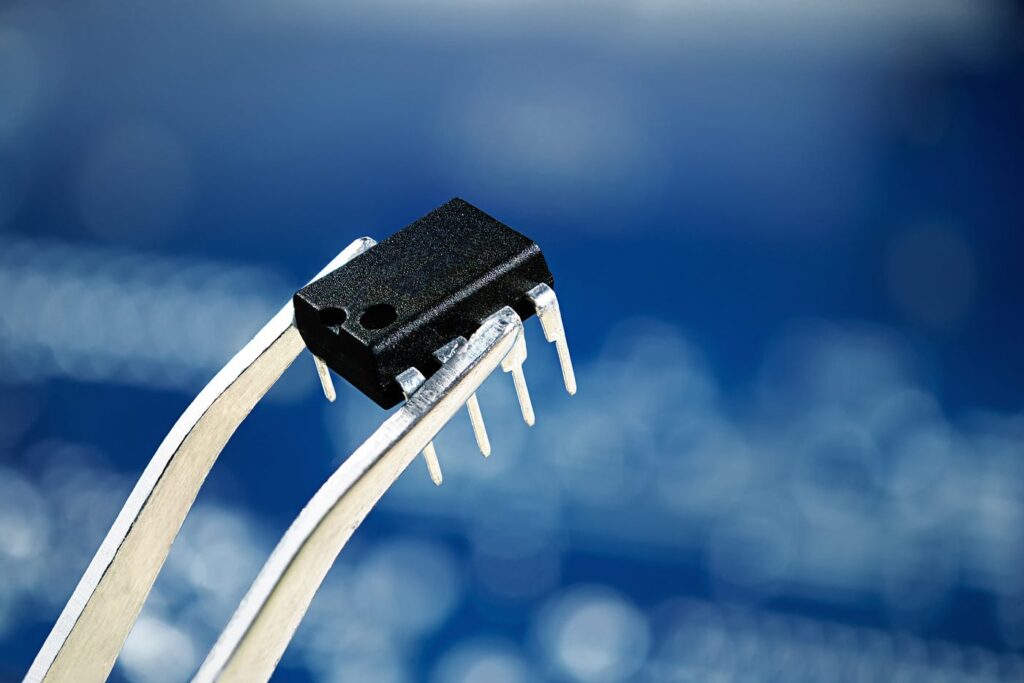
Unlocking a secured MCU GD32F101C8T6 embedded firmware
Unlocking a secured MCU GD32F101C8T6 embedded firmware is a challenging process that requires advanced technical knowledge in cracking or decrypting encrypted protections. This protective microcomputer incorporates sophisticated security features to prevent unauthorized access, safeguarding its firmware, binary data, and heximal code stored in flash memory and EEPROM memory. Successfully unlocking such a secured MCU often involves leveraging reverse engineering techniques to bypass these protective measures.
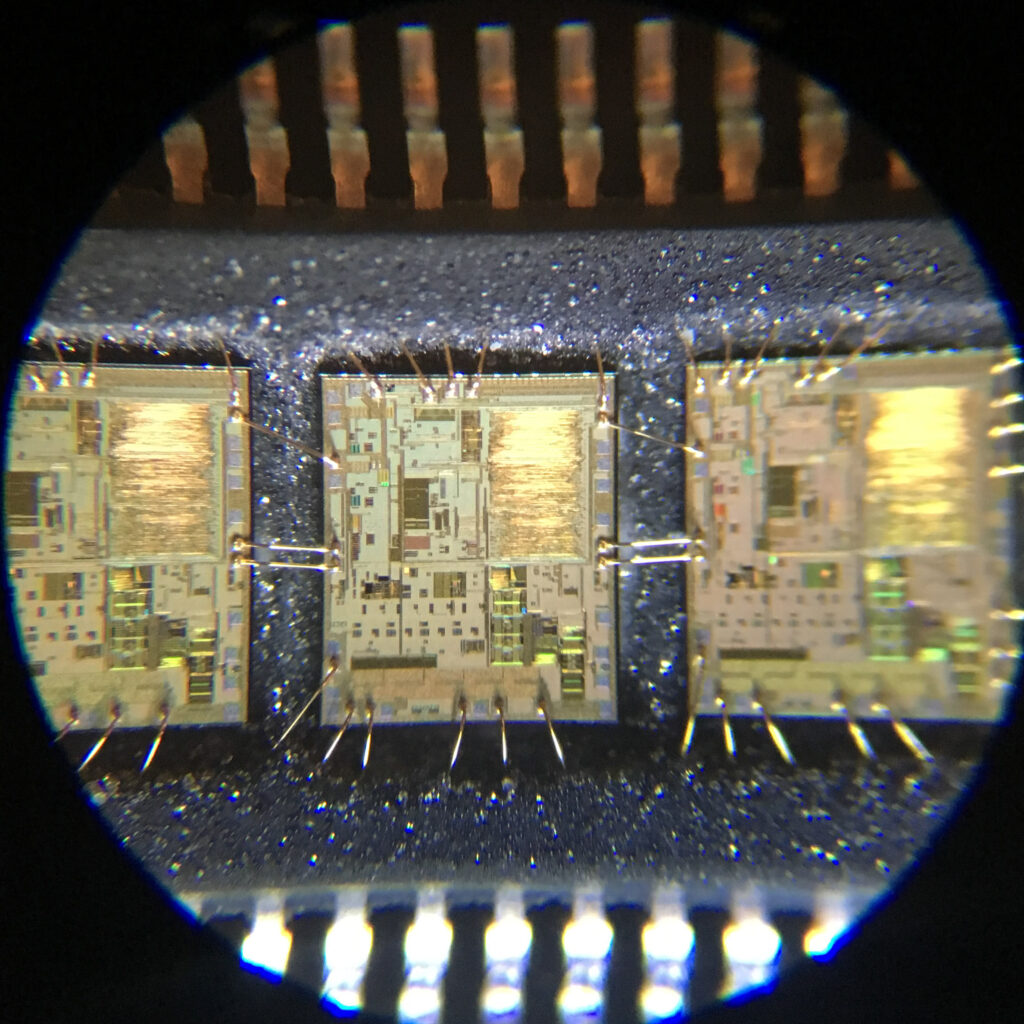
The process typically begins with analyzing the microprocessor’s architecture to understand how the encrypted protections function. Using specialized hardware and software tools, professionals attempt to crack the security layers and gain access to the locked firmware. This stage demands precision and expertise, as any mishandling could damage the microcontroller or compromise the embedded program.
Once the encryption is bypassed, the firmware can be recovered, copied, or cloned for authorized purposes. The binary or heximal data extracted from the GD32F101C8T6’s flash memory is crucial for restoring or replicating the software. For example, recovering lost or corrupted source code can help restore a system to its original functionality. Similarly, cloning the firmware enables the duplication of a microcontroller’s program, which can be essential for hardware replication, system diagnostics, or creating backups.
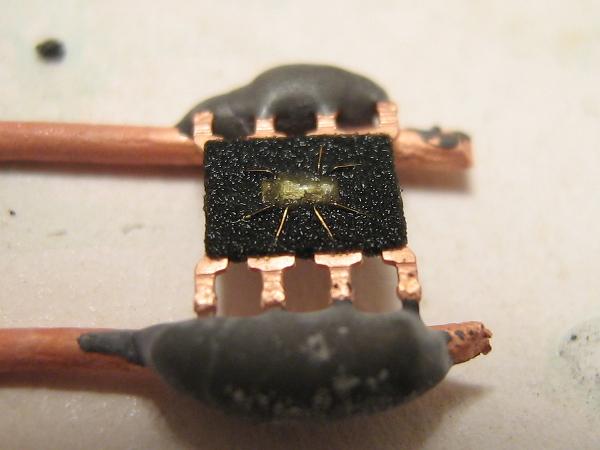
Additionally, reverse engineering the firmware provides insights into the underlying program and its functionalities. This can be useful for developers aiming to troubleshoot or enhance the software. However, unlocking a protective microcomputer like the GD32F101C8T6 requires compliance with ethical and legal standards, as embedded firmware is often protected by intellectual property laws.
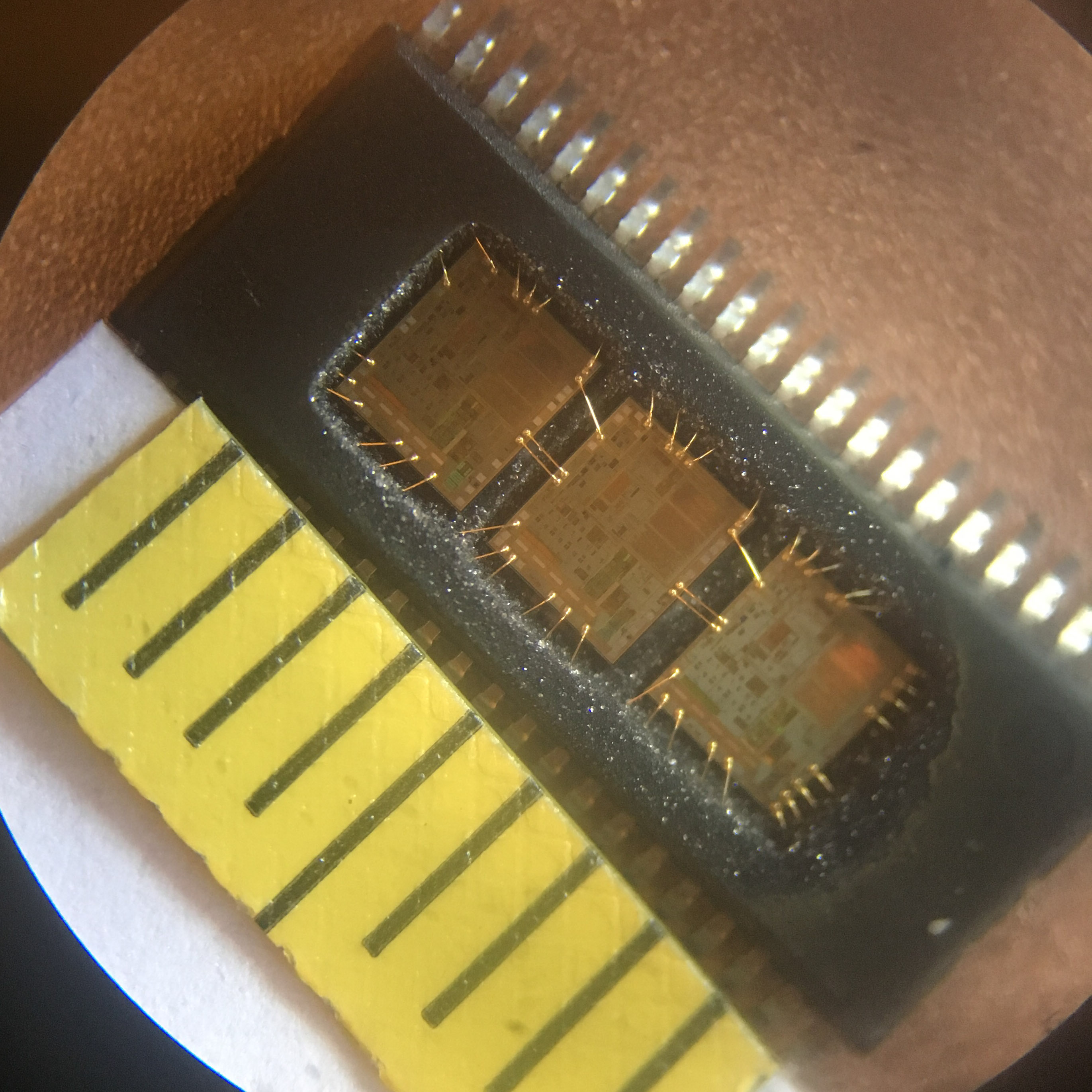
In summary, unlocking the secured MCU GD32F101C8T6 embedded firmware involves cracking encrypted protections, recovering binary and heximal data, and restoring or cloning its program. This process demands an in-depth understanding of secured MCUs and protective microcomputers, along with the use of advanced reverse engineering techniques. Proper handling ensures that the program’s integrity is preserved, making it possible to achieve system restoration, replication, or analysis while adhering to legal and ethical guidelines.