Unlock STM32F102C4 Microprocessor Embedded Memory
Methods to Unlock STM32F102C4 Microprocessor Embedded Memory
Voltage Glitching Attack
This technique involves applying controlled voltage fluctuations to the microcontroller during boot or runtime. The goal is to bypass the secured memory access restrictions, allowing unauthorized readout.
Success Rate: Moderate, depending on the precision of the attack.
Risk: High chance of permanently damaging the chip due to incorrect voltage application.
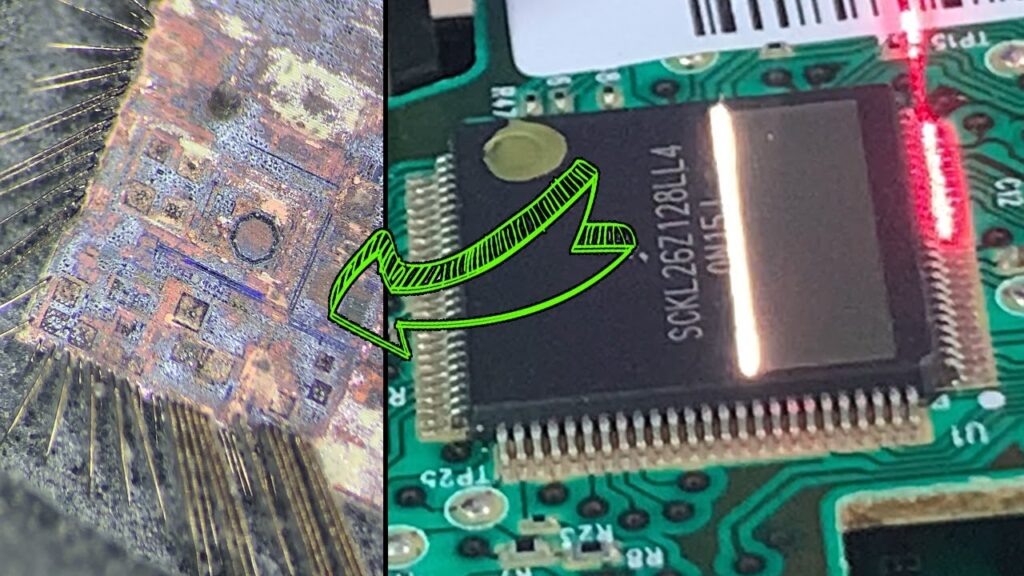
Decapsulation and Microprobing
In this method, the chip is chemically decapsulated to expose the internal circuitry. A fine probe is then used to access the flash memory directly, enabling the extraction of heximal or binary data.
Success Rate: High for skilled professionals with proper lab equipment.
Risk: Expensive, irreversible, and requires advanced hardware expertise.

Fault Injection Attack
Using electromagnetic or laser-based techniques, attackers introduce controlled faults into the MCU to temporarily disable security protections, allowing access to the protected firmware.
Success Rate: Moderate to high, depending on the equipment used.
Risk: Requires precision; improper handling may result in permanent corruption of memory.
Firmware Extraction via Debug Interface Exploits
Some STM32 microcontrollers may have vulnerabilities in the debug interface (SWD/JTAG), which can be exploited to decode and extract the encrypted firmware.
Success Rate: Varies based on the chip revision and security settings.
Risk: STMicroelectronics frequently patches such vulnerabilities in newer models.
General Process of Unlocking
- Initial Analysis – Identify the security level of the MCU and assess the feasibility of different attacks.
- Choosing an Attack Method – Based on available tools and expertise, select an appropriate method such as glitching, decapsulation, or debug exploit.
- Execution & Data Dumping – Apply the chosen technique and attempt to break the protection to obtain the firmware, heximal files, or source code.
- Post-Processing – Analyze the extracted data, decrypt if necessary, and replicate the original program.
Risks and Legal Considerations
- Hardware Damage – Many of these methods carry the risk of permanently damaging the microprocessor or corrupting the memory.
- Legal Consequences – Unauthorized attempts to hack or decrypt a locked STM32F102C4 may violate intellectual property laws. Ensure you have legal permission before proceeding.
- Security Updates – STMicroelectronics frequently enhances security, making some reverse engineering techniques obsolete in newer versions.
Conclusion
Unlocking an STM32F102C4 microprocessor embedded memory is a complex process requiring specialized knowledge and tools. While methods like voltage glitching, decapsulation, and debug exploits exist, each has its own risks and varying success rates. Before attempting to break the secured protections, it is crucial to assess the legality and technical feasibility of such actions.

The window watchdog is based on a 7-bit downcounter that can be set as free running which can provide great support to Unlock STM32F102C4 Microprocessor Embedded Memory. It can be used as a watchdog to reset the device when a problem occurs. It is clocked from the main clock. It has an early warning interrupt capability and the counter can be frozen in debug mode through the process of Break IC Memory.

This timer is dedicated for OS, but could also be used as a standard down counter. It features:
A 24-bit down counter
Autoreload capability
Maskable system interrupt generation when the counter reaches 0.
Programmable clock source
The I²C bus interface can operate in multimaster and slave modes. It can support standard and fast modes.
It supports dual slave addressing (7-bit only) and both 7/10-bit addressing in master mode. A hardware CRC generation/verification is embedded in the process of Unlock ATMEL MCU ATmega48A Firmware. The interface can be served by DMA and it supports SM Bus 2.0/PM Bus. The STM32F100xx value line embeds three universal synchronous/asynchronous receiver transmitters (USART1, USART2 and USART3).
The available USART interfaces communicate at up to 3 Mbit/s. They provide hardware management of the CTS and RTS signals, they support IrDA SIR ENDEC, the multiprocessor communication mode, the single-wire half-duplex communication mode and have LIN Master/Slave capability to Read IC PIC MCU PIC16F887. The USART interfaces can be served by the DMA controller.
Up to two SPIs are able to communicate up to 12 Mbit/s in slave and master modes in full- duplex and simplex communication modes for the purpose of ST ST62T10 Embedded Code Unlocking. The 3-bit prescaler gives 8 master mode frequencies and the frame is configurable to 8 bits or 16 bits. Both SPIs can be served by the DMA controller.

