STM32F100ZC CPU Memory Cracking
STM32F100ZC CPU memory cracking involves reverse engineering the secured and encrypted firmware stored within the CPU’s flash memory and EEPROM memory. This microcontroller unit (MCU) is designed with protective mechanisms to safeguard its binary, heximal, and program data. However, advanced techniques can be employed to crack and decode the locked memory for specific purposes like restoring functionality or cloning software.
To unlock the STM32F100ZC, experts analyze the microprocessor’s architecture to bypass encryption protocols and retrieve the embedded source code. This process enables the recovery of critical software that may be essential for repairing or replicating systems reliant on this MCU. Extracting the encrypted firmware also allows for cloning or restoring the original program for use in new devices or backups.
While STM32F100ZC CPU memory cracking can be valuable for recovering lost or damaged data, it must be performed within legal and ethical boundaries to respect intellectual property rights.

Unless otherwise specified the minimum and maximum values are guaranteed in the worst conditions of ambient temperature by STM32F100ZC CPU Memory Cracking, supply voltage and frequencies by tests in production on 100% of the devices with an ambient temperature at TA = 25 °C and TA = TAmax (given by the selected temperature range).
Data based on characterization results when Crack Microcontroller Chip IC Microchip PIC16F57, design simulation and/or technology characteristics are indicated in the table footnotes and are not tested in production. Based on characterization, the minimum and maximum values refer to sample tests and represent the mean value plus or minus three times the standard deviation (mean±3s) in order to Duplicate MC68HC11K1 MCU Locked Program.

Unless otherwise specified, typical data are based on TA = 25 °C, VDD = 3.3 V (for the 2 V £ VDD £ 3.6 V voltage range). They are given only as design guidelines and are not tested.
Typical ADC accuracy values are determined by characterization of a batch of samples from a standard diffusion lot over the full temperature range for the purpose of Crack Chip Protected PIC18F2550 Heximal, where 95% of the devices have an error less than or equal to the value indicated (mean±2s).
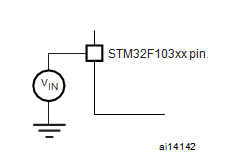
Unless otherwise specified, all typical curves are given only as design guidelines and are not tested before Attack Microprocessor IC Microchip PIC18F4431. The loading conditions used for pin parameter measurement are shown in below figure.
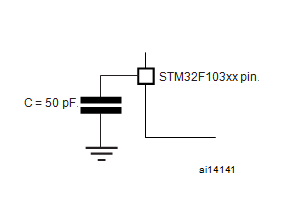
The input voltage measurement on a pin of the device is described in below figure which will provide the great support for Reverse Engineering Microcontroller: