Secured Microprocessor GD32F101D4T6 Flash Program Decryption
Secured Microprocessor GD32F101D4T6 Flash Program Decryption involves cracking the encrypted protections of this advanced microcontroller to access its embedded firmware. This protective microcomputer is engineered to safeguard its flash memory, EEPROM memory, and binary data, ensuring its program and source code remain locked against unauthorized access. To unlock or decode the secured firmware, reverse engineering is a critical technique used to break the defensive layers implemented within the microprocessor.
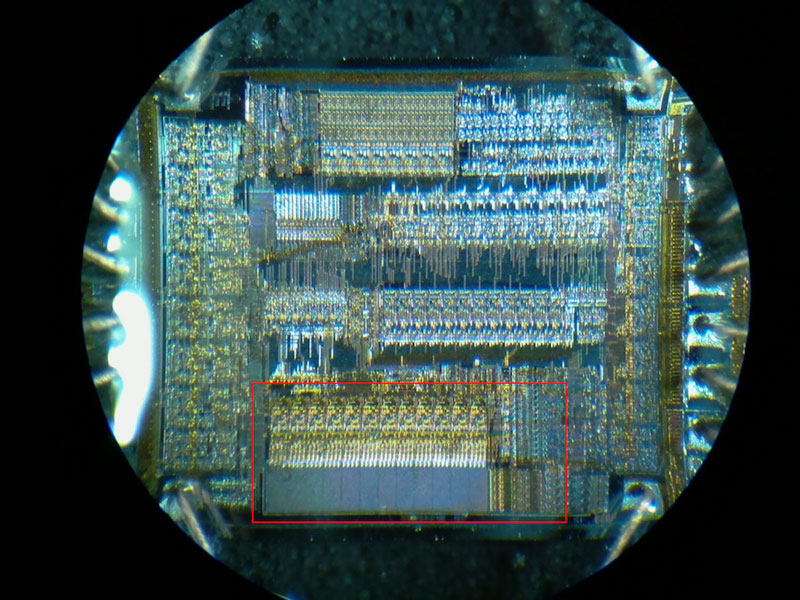
The process typically begins with an in-depth analysis of the microcontroller’s architecture to understand its encryption and protective mechanisms. By decoding the heximal or binary structure of the GD32F101D4T6, professionals can identify potential vulnerabilities that enable access to its locked firmware. Advanced tools and techniques are often required to clone or restore the embedded program without damaging its original integrity.
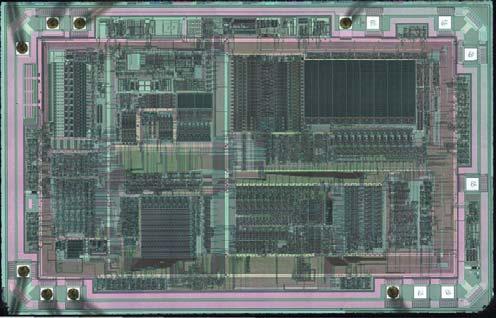
Once the secured microprocessor’s flash memory is unlocked, the extracted software or source code can be recovered and restored for legitimate purposes. This may include duplicating the program for hardware replication, creating backups, or performing system diagnostics. Cloning the firmware also provides opportunities for developers to analyze the code for improvements, troubleshooting, or compliance testing.
Despite the technical challenges, the decryption of the GD32F101D4T6 flash program is critical in scenarios where restoring or recovering lost data is necessary. However, breaking the secured protections of such a locked microcontroller must be carried out within legal and ethical boundaries. Unauthorized decryption, cloning, or copying of the software or firmware may violate intellectual property rights and lead to significant legal consequences.
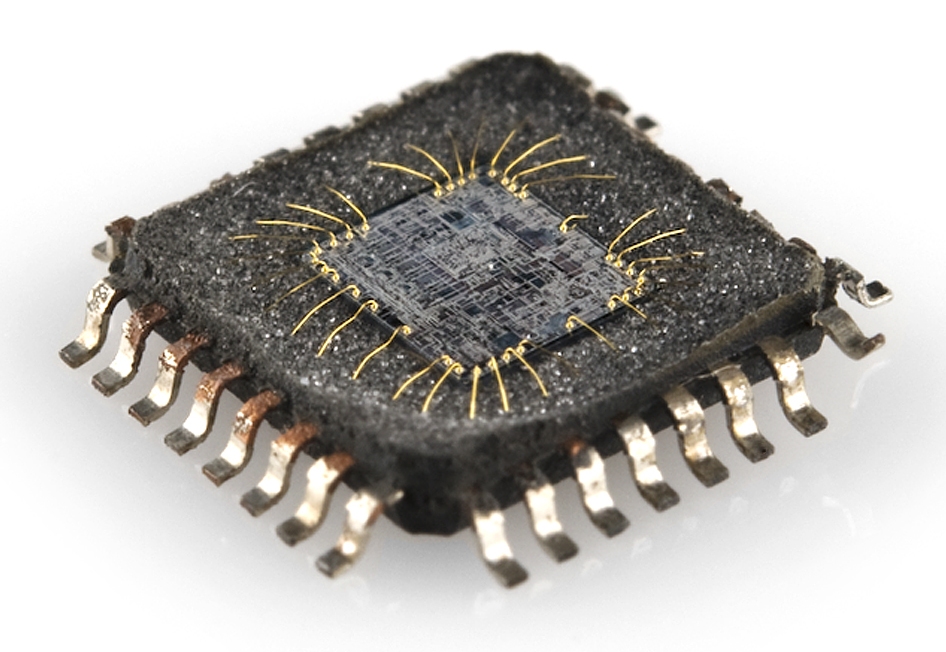
In conclusion, the decryption of the GD32F101D4T6 flash program requires cracking encrypted protections, decoding the binary or heximal firmware, and utilizing reverse engineering to access its locked software. The ability to unlock and clone this secured microprocessor is essential for restoring or replicating critical systems. However, adherence to legal standards is paramount to ensure the process is both effective and responsible, safeguarding intellectual property while achieving the desired outcomes.


