Microcontroller Extraction Technology
Microcontroller Extraction Technology
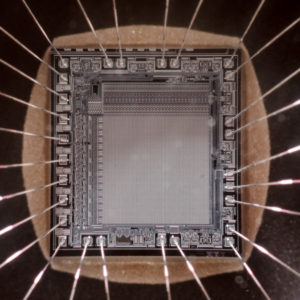
Microcontroller extraction technology has developed over the last decades and the next advancement is placing the EEPROM chip into the same package of microcontroller.
It is not easy to extract the firmware out from microcontroller. One of the professional method is de-capsulate the package of microcontroller and extract the firmware by using microprobe or solder the microcontroller into a different package, both of these methods are not cheap for the low level attacker to proceed the extraction.
They will only extract the firmware by the home-made microprobe and take advantage of the flaw on the software of microcontroller to extract the data.
Some microcontroller all along has not any special security protection against the extraction since they only protect by un-public programming algorithm which probably has read-back functions of microcontroller extraction or use validation function to replace it.
But these microcontroller won’t provide great protection against extraction, in some of the smart card, the application of validation function can provide very good protection for microcontroller extraction.
The next step of microcontroller extraction development is add a hardware security fuse so call storage to prohibit the unauthorized access to the data which is easy to proceed since the design is not need to redesign the microcontroller structure.
They use only the read back function of control programming interface. The drawback of security fuse is too easy to be located and then proceed the attack for microcontroller extraction, for example, the status of security fuse can be modified through the direct connection of output of security fuse bit to power supply or grounding.
Some of them can even just cut the sensing circuit of security fuse by laser or focus ion beam to extract the microcontroller.