Decrypt secured MCU GD32F101C4T6 program
Decrypting a secured MCU GD32F101C4T6 program is a highly technical process that involves bypassing the protective mechanisms implemented by the microcontroller. The GD32F101C4T6, like many modern microcontrollers, uses encryption to safeguard its firmware, preventing unauthorized access to the underlying source code.

In such scenarios, experts in reverse engineering are often employed to crack the security, with the goal of decrypting the encrypted program and gaining access to its binary or hexadecimal code. This process, while challenging, is often necessary when restoring lost firmware or creating compatible systems.
Locked microcontrollers, such as the GD32F101C4T6, are designed to prevent tampering or unauthorized copying of the software they contain. The firmware stored within these devices is often proprietary and critical to the device’s operation.
To crack this protection, engineers must analyze the architecture of the microcontroller and identify potential vulnerabilities that allow them to decrypt or bypass the encryption layers. This often requires understanding the binary and hexadecimal formats in which the firmware is stored, as well as being able to decode and interpret these data formats effectively.
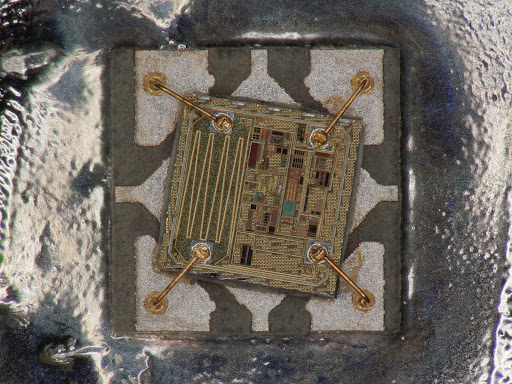
One key aspect of this process is the restoration of original firmware. In cases where the program has been lost or damaged, reverse engineering and decryption can be used to restore the original code, ensuring that the system can continue functioning as intended.
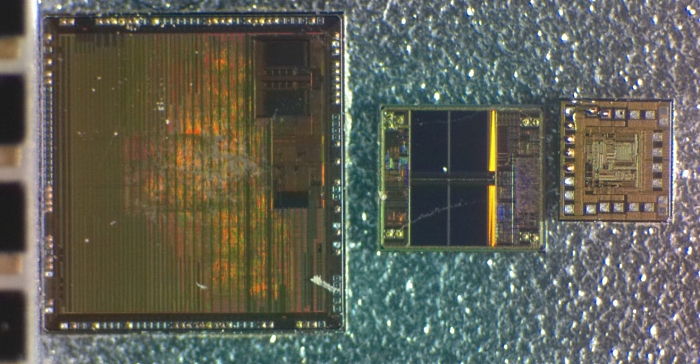
However, the process of decrypting secured MCU programs also raises ethical concerns, especially when the intention is to copy proprietary firmware for use in other projects or products without authorization.
While some engage in this practice to recover lost source code or repair malfunctioning systems, others may attempt to copy the firmware for financial gain, violating intellectual property rights. Locked microcontrollers like the GD32F101C4T6 are built with protective measures precisely to prevent such unauthorized access.
As encryption technologies advance, the task of cracking and decrypting secured microcontrollers becomes increasingly difficult, requiring deep technical expertise in microprocessors, encryption methods, and reverse engineering.


