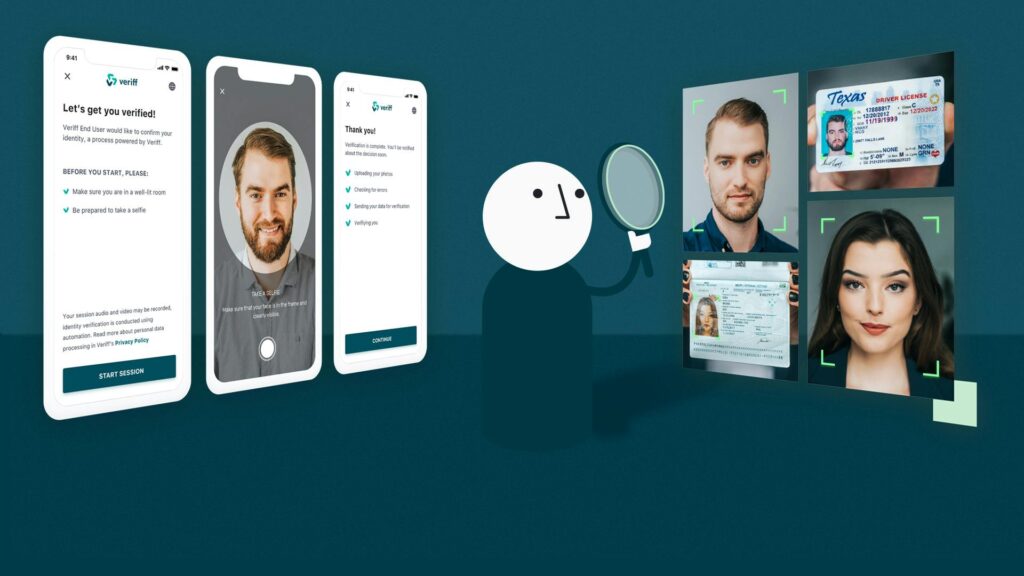
Bypassing 2FA Network Authentication Service
In the world of network authentication, two-factor authentication (2FA) is widely regarded as one of the most effective methods for enhancing security. By requiring two forms of verification — something the user knows (a password) and something they...
The Service for Brute Force Attack Over Network Authentication: A Growing Threat
In the ever-evolving field of network authentication, brute force attacks represent a significant threat to systems that rely on password-based security. These attacks are often used to hack into systems by systematically trying every possible passw...
Password Cracking Service for Network Authentication: A Growing Threat
In the realm of network authentication, securing passwords is a fundamental practice to prevent unauthorized access to sensitive systems. However, malicious actors often employ password cracking services to bypass authentication systems, breaking or...
Cracking Network Authentication Services: Risks and Protections
In today’s interconnected world, network authentication is the first line of defense against unauthorized access to sensitive systems and data. It ensures that only legitimate users can interact with network resources. However, malicious actors ofte...