Attacking Chip Unpredictability
Another area of possible concern could be in unpredictability of the new attacking chip methods, especially if they would be based on some methods previously thought to be impossible. There were many examples when some new attacks were discovered based on already known facts. This requires the chip manufacturers and developers to find ways of predicting such chip attacks and developing mitigation techniques well ahead of any active use by MCU attackers.
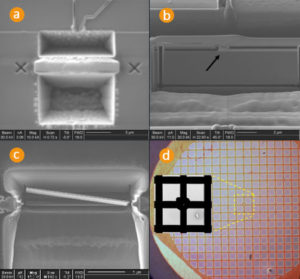
Recently demonstrated methods for the direct imaging of EEPROM and Flash memory contents using SEM pose big challenges to the hardware security. Not only because non-volatile memory was always considered as being highly secure against invasive microcontroller attacks, but also because there are no mitigation techniques to defeat this unless new methods of storage are developed. Now the obvious question is: What could be the next in ground breaking and disturbing attacking chip on hardware security?
In case of microcontroller cracks disclosure there is always a dilemma for the best way of responsible disclosure. There are no strict rules on that, hence, both chip manufacturers and researchers could be affected. On one hand, the researchers want to tell everyone about their findings and make sure they found something important ahead of anyone else. On the other hand, developers want to avoid large recall of their products for updates or, worse, replacement. The solution could be in working together on the development of mitigation techniques.