Locked ARM Cortex STM32F103C4 MCU Cracking
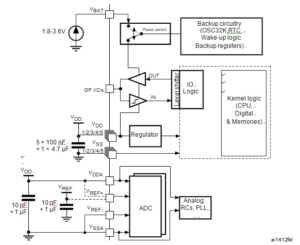
The temperature sensor has to generate a voltage that varies linearly with temperature to Recover MCU content. The conversion range is between 2 V < VDDA < 3.6 V. The temperature sensor is internally connected to the ADC1_IN16 input channel which is used to convert the sensor output voltage into a digital value by Locked ARM Cortex STM32F103C4 MCU Cracking.
The ARM Cortex STM32F103C4 microcontroller (MCU) is widely used in embedded systems, but its security features often make it difficult to extract or modify its firmware. When the MCU is locked or secured, accessing its internal memory, including the flash or EEPROM, becomes a challenging task. However, using techniques like reverse engineering, it’s possible to unlock or break the protection and recover valuable data from the chip.

One common approach is to attack the MCU by exploiting vulnerabilities in the system or using physical methods to extract the binary files. For example, dumping the contents of the memory or microprocessor can provide access to the source code or encrypted program stored within. Once the data is extracted, hackers may decode or decrypt the binary to replicate or clone the firmware for other applications.
Reverse engineering is key in this process, where professionals analyze the chip’s architecture and analyze the encrypted data to decode the firmware. In some cases, even with the most secured protection mechanisms, a determined effort can break the encryption and unlock the program for further manipulation.
In conclusion, cracking the locked STM32F103C4 MCU requires a combination of specialized tools, techniques, and persistence, as well as an understanding of how to bypass its protection to gain access to sensitive data.
The ARM SWJ-DP Interface is embedded, and is a combined JTAG and serial wire debug port that enables either a serial wire debug or a JTAG probe to be connected to the target of STMicro STM32F101RB MCU Cracking. The JTAG TMS and TCK pins are shared respectively with SWDIO and SWCLK and a specific sequence on the TMS pin is used to switch between JTAG-DP and SW-DP.
Unless otherwise specified the minimum and maximum values in the process of Unlock ARM Base STM32F101CB Microprocessor are guaranteed in the worst conditions of ambient temperature, supply voltage and frequencies by tests in production on 100% of the devices with an ambient temperature at TA = 25 °C and TA = TAmax (given by the selected temperature range).
Data based on characterization results, design simulation and/or technology characteristics are indicated in the table footnotes and are not tested in production for the purpose of Clone STM32F101C8 MCU Memory Data. Based on characterization, the minimum and maximum values refer to sample tests and represent the mean value plus or minus three times the standard deviation (mean±3S).
Unless otherwise specified, typical data are based on TA = 25 °C, VDD = 3.3 V (for the 2 V £ VDD £ 3.6 V voltage range). They are given only as design guidelines and are not tested.
Typical ADC accuracy values are determined by characterization of a batch of samples from a standard diffusion lot over the full temperature range from Locked ARM Cortex STM32F103C4 MCU Cracking, where 95% of the devices have an error less than or equal to the value indicated (mean±2S).