ARM Microcontroller STM32F103C6 Memory Unlocking
The STM32F103C6, a popular ARM microcontroller, often features secured memory to protect firmware and critical data from unauthorized access. However, through techniques like reverse engineering, it’s possible to crack or hack the encrypted memory, extracting vital files or binary data stored within the chip. By leveraging tools designed to dump or decode flash memory, one can unlock the microcontroller’s protected content, including eeprom and program data.

Memory attacks may involve exploiting vulnerabilities in the MCU’s firmware, allowing hackers to break encryption or replicate the source code embedded in the chip. With the right knowledge, it’s possible to recover and clone the locked data, bypassing the microcontroller’s security mechanisms. Tools for dumping or decoding data can often decrypt the protected memory, making it accessible for further analysis or exploitation.
Understanding these methods requires technical expertise in microprocessors and memory architectures to successfully decode and extract the required information.
The current consumption is a function of several parameters and factors such as the operating voltage, ambient temperature, I/O pin loading, device software configuration, operating frequencies, I/O pin switching rate, program location in memory and executed binary code extracted from the process of Microntroller ST62T40 Flash Program Cloning.

The current consumption is measured as described in Figure 11: Current consumption measurement scheme.
All Run-mode current consumption measurements given in this section are performed with a reduced code that gives a consumption equivalent to Dhrystone 2.1 code for the purpose of Unlock TMS320F28022 Microcontroller Flash Data.
The MCU is placed under the following conditions:
- l All I/O pins are in input mode with a static value at VDD or VSS (no load)
- l All peripherals are disabled except if it is explicitly mentioned
- l Prefetch in on (reminder: this bit must be set before clock setting and bus prescaling)
- l When the peripherals are enabled fPCLK1 = fHCLK, fPCLK2 = fHCLK
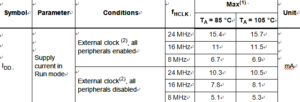
The parameters given in below Table are derived from tests performed under the ambient temperature and VDD supply voltage conditions summarized from ARM Microcontroller STM32F103C6 Memory Unlocking.
The Recovering MCU is placed under the following conditions:
- All I/O pins are in input mode with a static value at VDD or VSS (no load)
- All peripherals are disabled except if it is explicitly mentioned in the process of Crack Chip PIC18F2410 Dump
- When the peripherals are enabled fPCLK1 = fHCLK, fPCLK2 = fHCLK, fADCCLK = fPCLK2/2

